A common use case for IAM Role is to allow an IAM user in one AWS account to access resources in another AWS account. By using a IAM role, you can avoid distributing lots of long term credentials like user name, password or access keys.
AWS IAM Role – Cross Account
Use Case
Let’s start with 2 AWS accounts: Stuzio account (081278057606) and Acme account (183438944504). There is an IAM user named Troy in the Acme account that needs access to S3 bucket objects in the Stuzio account. The goal is to grant Troy access using an IAM role. Troy will log into Acme’s account using his Acme IAM user credential then assume a Stuzio IAM role to access the S3 bucket resource in the Stuzio account. Notably, we will NOT create an IAM user for Troy in the Stuzio account and hand out a user name/password or access key to Troy.
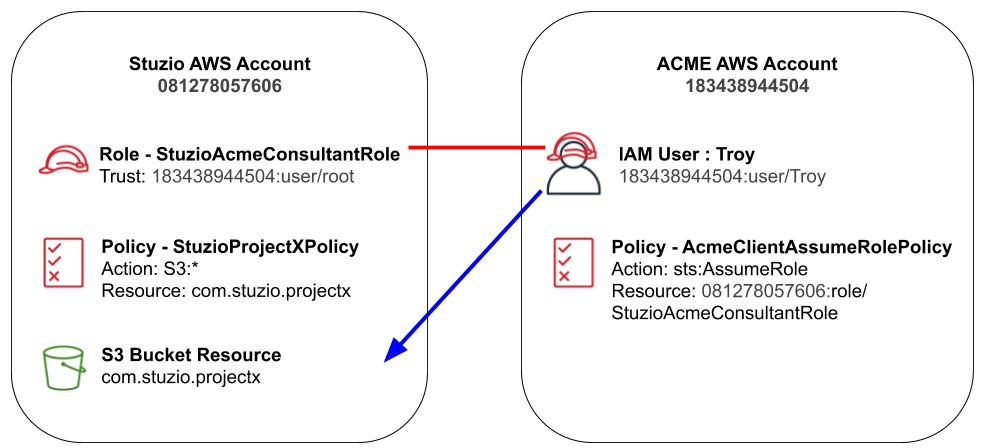
The solution uses the following resources and configuration.
IAM Role - StuzioAcmeConsultantRole
An IAM Role in the Stuzio account named StuzioAcmeConsultantRole. The purpose of this role is to allow consultant IAM users from Acme account access to the Stuzio resources. The role has a trust relationship with Acme’s IAM user specified by the arn “arn:aws:iam::183438944504:root” which references all IAM users from the Acme account. The root notation at the end means all IAM user from Acme account 183438944504. The role has StuzioProjectx policy attached.
IAM Policy - StuzioProjectXPolicy
This policy in the Stuzio account allows full access to S3 bucket resource “com.stuzio.projectx” which is needed for consultants working on project x. It also allows ListAllMyBucket action which simply allows the user to view the list of buckets. This is added for demonstration purpose so users can see the available buckets when logged into the AWS management console.
S3 Bucket - com.stuzio.projectx
This is the S3 resource in the Stuzio account that Troy from Acme account needs access. The bucket contains several objects. The bucket does not have any resource policy.
}
IAM User - Troy
This is an IAM User created in the Acme account. Troy can log into the AWS management console using the IAM User’s username and password as credential. The IAM has only 1 policy attached called AcmeClientAssumeRolePolicy
IAM Policy - AcmeClientAssumeRolePolicy
This policy in the Acme account is attached to IAM User Troy. The purpose of this policy is to allow Troy to assume a role which required security token service assume role action (sts:AssumeRole). The resource on this statement is referencing the IAM Role “StuzioAcmeConsultantRole” that’s in the Stuzio account.
Summary
This pattern can be used to allow many Acme IAM users access to Stuzio resources without having to create individual IAM users in the Stuzio account. Similar pattern is used to integrate a 3rd party SaaS solution that needs access across accounts.
If you want to learn more about IAM role and other practical applications of IAM, check out the course AWS Identity and Access Management – Practical Applications. This course covers core features of IAM including user, group, principal and role with lots of demonstration of practical use cases.

